Brocade VDX First Impressions.
I recently had the opportinity to work with the much-anticipated Brocade VDX “Ethernet Fabric” platform. I do admit tha tI’m intrigued by this product. I’d seen it work multiple times in demos and it worked so well and looked to easy that we actively tried to throw curve balls at the demo organizer to prove it wasn’t canned.
 It succeeded.
The hardware hashing across the VLAGs is very slick. The VMware VSwitch integration worked well and was handy. With the movement to virtualization, this is an important piece for most data center folks.
That being said, some people have very specific data center requirements that aren’t really the same as an enterprise. For example:
It succeeded.
The hardware hashing across the VLAGs is very slick. The VMware VSwitch integration worked well and was handy. With the movement to virtualization, this is an important piece for most data center folks.
That being said, some people have very specific data center requirements that aren’t really the same as an enterprise. For example:
- Don't firewall everything at the DC. That's right. I said it. Firewalls don't solve all security problems. Take that "defense in depth"!
- A potential need to do non-standard or experimental protocols.
- A lot of line rate 10G internally and to the rest of network.
- Integration with legacy, existing and or in-house written tools
- Need for GSLB/SLB
- Self Healing
- Ease of fabric upgrade (software upgrade doesn't cause fabric isolation)
- Ease of fabric upgrade (increase LAG numbers and capacity easily)
- Multi-Homed hosts
- IPv4
- IPv6
- IPv4 Multicast
- Future SDN support
- NAT
- Public Address space
- All at the same time
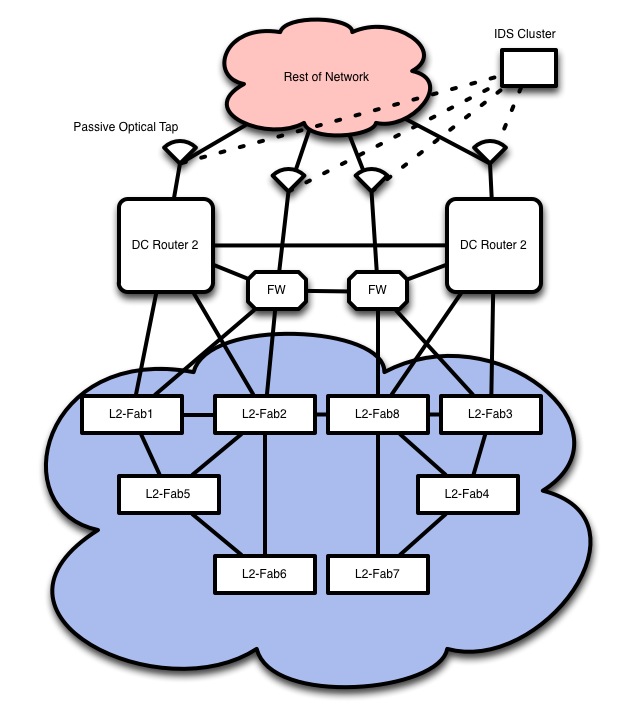
But I digress. We can get into the Data Center design details later. Below would be a theoretical data center reference design for a fabric deployment. Please bear in mind that I mostly like to focus on the WAN and SP bits, so take my data center speculations and musings with a grain of salt.
The Brocade VDX does most of what can be expected of a layer 2 fabric. It really is the “easy” part of a DC design. If you can avoid STP, I would heavily recommend it. I have an unnatural dislike for spanning tree.
The unexpected things I ran into with my very brief hands-on with the VDX were just that, unexpected. I could reliably crash ssh on the boxes by sending a public key at login, which is default behavior for a normal ssh client. This was very annoying and implied that they don’t yet support ssh keys for authentication. One can work around it by doing *ssh -o PubkeyAuthentication=no -l